Uncovering Security Blind Spots in CNC Machines

Industry 4.0 has given rise to smart factories that have markedly improved machining processes, but it has also opened the doors for cybercriminals looking to abuse networked industrial equipment such as CNC machines. Our research investigates potential cyberthreats to CNC machines and how manufacturers can mitigate the associated risks.
Read time: ( words)
The Fourth Industrial Revolution, more commonly known as Industry 4.0, has changed the way factories operate. It has heralded the adoption of relatively novel technologies that empower companies to optimize many aspects of manufacturing, including industrial machinery such as computer numerical control (CNC) machines. These machines play a crucial role in production lines, as they wield tools on different axes that allow them to fashion complex parts with speed and precision. CNC machines can move according to their controllers’ parametric programs that can be easily modified to specifications, so a machine running one program can be used to create a whole range of products.
Under Industry 4.0, diverse pieces of manufacturing equipment like CNC machines now come with features that enable network integration and smart connectivity, resulting in reduced downtime and faster turnaround times for manufacturers. But innovation cuts both ways: As they become the norm, connected factories inadvertently become appealing targets for cyberattackers looking to sabotage the operations of, steal valuable data from, or spy on smart manufacturing environments. It’s therefore vital for manufacturers to be aware of any dangers that could arise from the interconnectivity of industrial machinery.
In our research, we carried out a range of attack scenarios against CNC controllers using both simulations and real-world machine installations. We conducted our tests on CNC controllers from four vendors that we selected for their worldwide reach and extensive market experience, or for developing technologies that are widely used in the manufacturing industry. The Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) of the Cybersecurity and Infrastructure Security Agency (CISA) also provided us with invaluable assistance as a liaison during our discussion with these vendors. As part of our thorough disclosure process, we reached out to the affected vendors in a timely manner, contacting the first back in November 2021. Since then, all of the vendors have taken steps to provide their end users with more secure solutions by improving their documentation, their communication with their respective machine manufacturers, or bettering their security posture by patching vulnerabilities and adding more security features to their offerings. We shared with these vendors the findings from our research, through which we identified various attack classes. In this blog entry, we discuss several potential attacks that fall under these classes, as detailed in Table 1.
| Attack class | Attack | Haas | Okuma | Heidenhain | Fanuc | Total |
| Compromise | Remote code execution | √ | √ | √ | 3 | |
| Damage | Disabling feed hold | √ | 1 | |||
| Disabling single step | √ | √ | 2 | |||
| Increasing the tool life | √ | √ | √ | 3 | ||
| Increasing the tool load | √ | √ | √ | 3 | ||
| Changing the tool geometry | √ | √ | √ | √ | 4 | |
| Denial of service | Decreasing the tool life | √ | √ | √ | 3 | |
| Decreasing the tool load | √ | √ | √ | 3 | ||
| Changing the tool geometry | √ | √ | √ | √ | 4 | |
| DoS via parametric program | √ | √ | √ | √ | 4 | |
| Triggering custom alarms | √ | √ | 2 | |||
| Ransomware | √ (network share) | √ (network share or THINC API) | √ (network share) | 3 | ||
| Hijacking | Changing the tool geometry | √ | √ | √ | √ | 4 |
| Hijacking a parametric program | √ | √ | √ | √ | 4 | |
| Program rewrite | √ | √ | √ | 3 | ||
| Data theft | Theft of production information | √ | √ | √ | √ | 4 |
| Theft of program code | √ (MTConnect or THINC API) | √ (DNC) | √ (FOCAS) | 3 | ||
| Theft via screenshots | √ | 1 | ||||
| Total | 15 | 14 | 15 | 10 |
Attacks that could cause damage
The tools used by CNC machines are measured for their geometry, such as their length and radius, to make sure these tools are suited to producing a specific piece. These measurements are taken by human operators or are done automatically during a CNC machine’s tuning phase. However, tampering with these measurements is one way in which malicious actors could cause damage to the machine itself, its parts, or the piece it’s working on. We found that all four CNC controller vendors that were part of this research were susceptible to this kind of attack. In one attack scenario, we created a 3D-printed plastic tool to demonstrate how a CNC machine’s tool could crash against the raw piece it’s working on because of negative overflow, after we set the CNC controller’s wear value to –10 mm (Figure 1).
Denial-of-service attacks
In this section, we discuss threat scenarios in which attackers attempt to drive down a manufacturer’s efficiency by sabotaging its production process. Of the attack classes outlined in our research, the denial-of-service (DoS) category has the largest number of potential attacks, including:
Triggering custom alarms
False alarms are another way malicious actors could disrupt the manufacturing process. CNC machines have built-in alarms that warn of faulty conditions in hardware, but they can also be configured with custom alarms for errors in software. When these alarms are set off, the CNC machine stops operating and needs a human operator’s intervention to continue. An attacker who has infiltrated a connected factory could trigger these software-related alarms, abruptly interrupting production. CNC controllers from two vendors involved in this research were exposed to this attack.
Changing the tool geometry
A CNC machine’s tool geometry gradually changes; its cutting edge, for one, becomes duller from continuous use. A CNC machine uses the “wear” parameter to compensate for such changes over time and reposition the tool so it can maintain the quality of the pieces in production. Malicious actors could mount different kinds of attacks, including DoS, by simply altering a tool’s geometry. For example, an attacker could configure a vertical milling machine’s wear parameter to be more than the length of the tool itself, which would instruct the mill to operate in midair, unable to touch the piece. Our tests revealed that CNC controllers from all four vendors that we tested were exposed to this kind of attack.
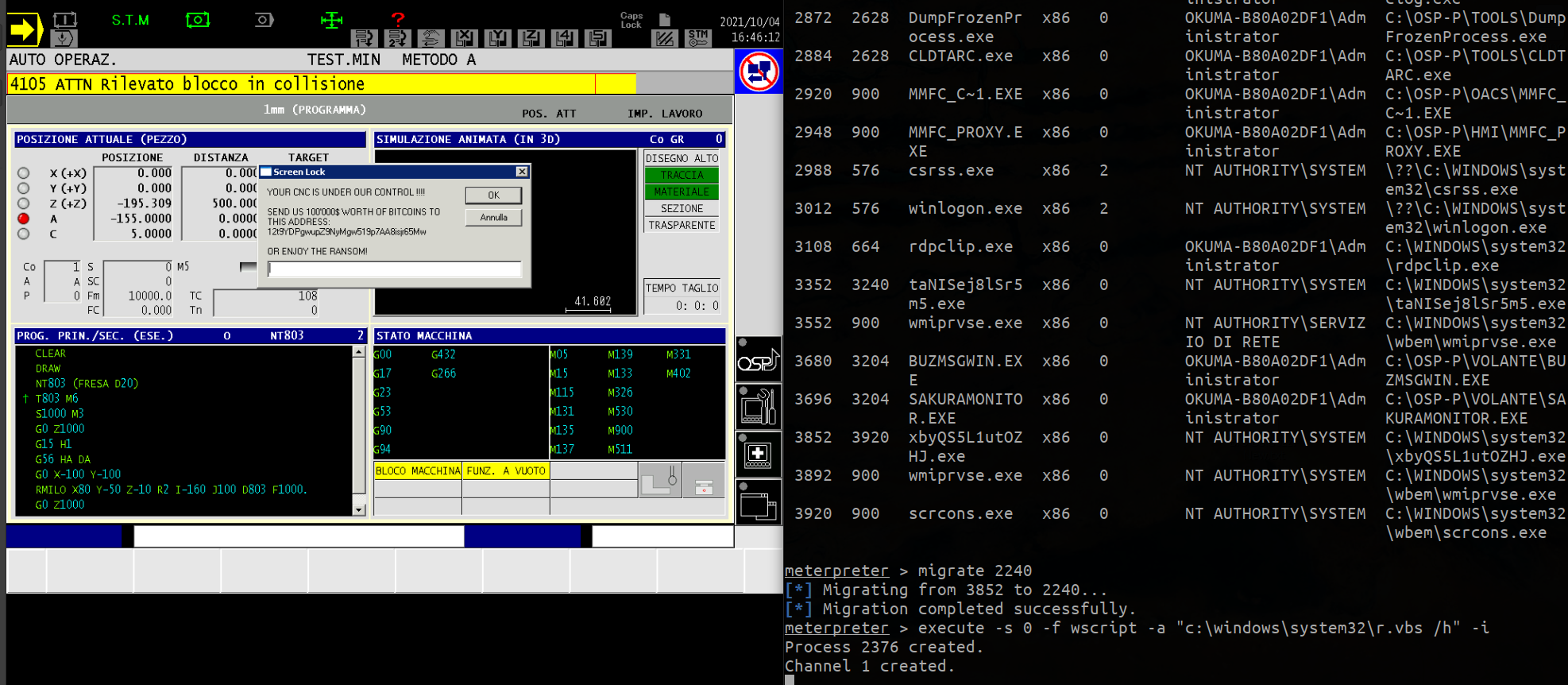
Ransomware
Not even CNC machines are immune to ransomware attacks. In one scenario, malicious actors could lock down a CNC machine or encrypt its files, effectively stopping production until the manufacturer meets their demands. Attackers could carry out a ransomware attack by using an unauthenticated network share to access a CNC machine’s files, abusing a malicious application to make operating system calls, or planting a script in a machine to lock its screen (Figure 2). Our results showed that machines from three of the four controller vendors that we tested were at risk of ransomware attacks.
Hijacking
Attackers seeking to control the production process could do so by hijacking a CNC controller. There are different ways malicious actors could carry out hijacking attacks, such as:
Changing the tool geometry
In this kind of attack, a malicious actor with extensive knowledge of the manufacturing process could seize control of a CNC controller to misconfigure its tool geometry in such a way that would lead to micro-defects in produced pieces. As part of an attack scenario, we developed a program instructing a CNC machine to engrave traces 5.05 mm deep in a piece of raw metal and were able to conduct attacks that modified the program’s wear parameters so that the CNC machine makes engravings that were only 4.80 mm in depth (Figure 3). Flaws such as this would be so minimal that they might slip past quality control measures, resulting in a costly product recall or a blow to the reputation of a manufacturing company. We found that all four CNC controller vendors that we tested were at risk of this kind of hijacking attack.

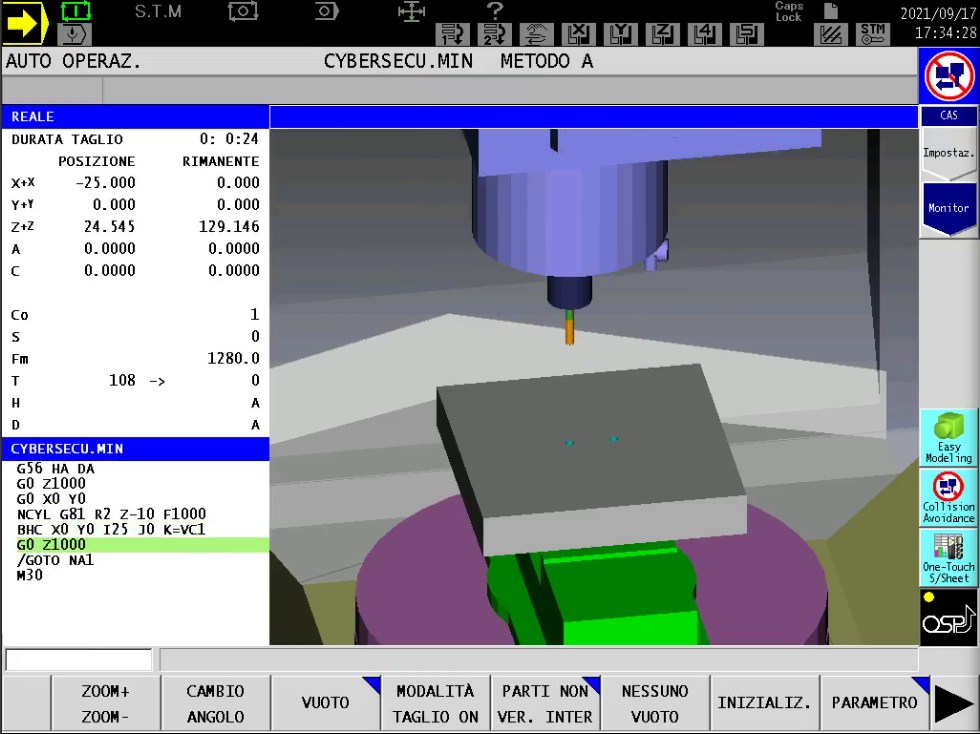
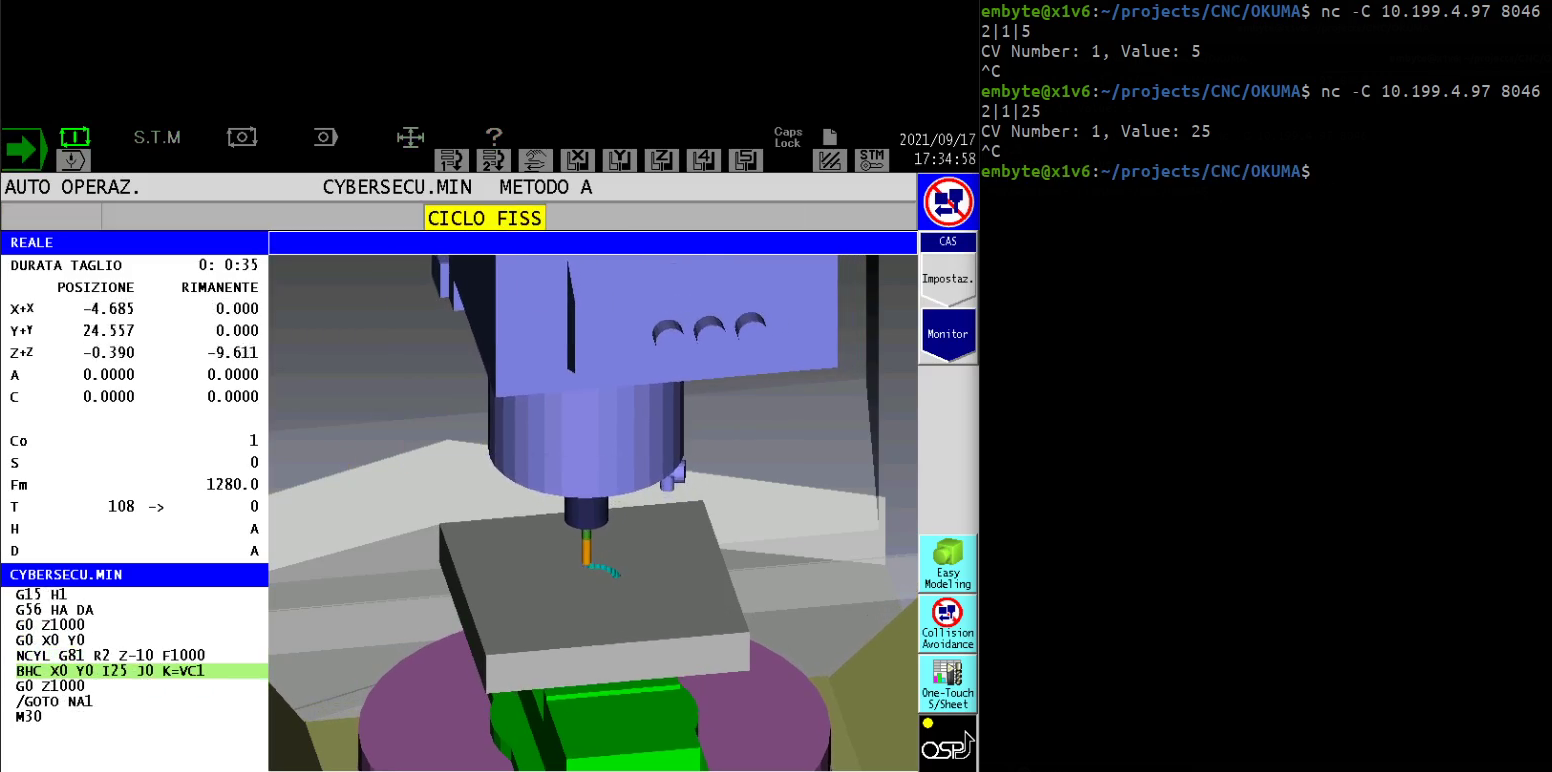
Hijacking parametric programs
Another way a malicious actor could introduce defects in pieces is by hijacking a CNC controller’s parametric program. To do this, an attacker would need to set a program’s variables to an arbitrary value, which would alter the pieces in a way that would fail to meet product specifications. For example, we simulated such an attack on a CNC controller and were able to modify a parametric program designed to make a tool drill two holes (Figure 5) and instruct the tool to instead drill 25 holes (Figure 6). Machines from all four vendors involved in this research were vulnerable to this kind of attack.
Data theft
There’s a wealth of data in CNC controllers that might attract the attention of malicious actors, who could attempt to access this information by various means. These attacks include:
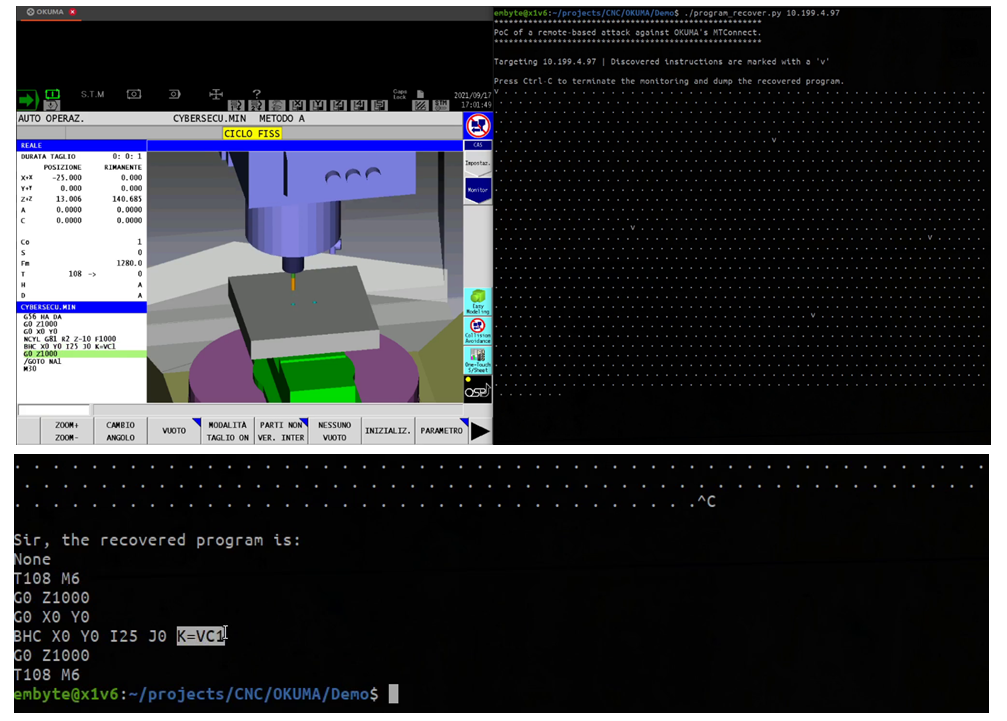
Theft of program code
The programs used to maneuver CNC machines are among a manufacturer’s most sensitive intellectual property, as these contain the details of how to make a specific part. Attackers could remotely access a program that a CNC controller is running by way of an unprotected network that the CNC controller is connected to, or by installing a malicious application in the machine’s controller. And because they’re written in G-code and are not compiled, these programs are easy to reverse-engineer. In one of our experiments, we found that an exposed MTConnect interface used to monitor CNC machines might also be abused by attackers, who could pool this service to pilfer the source code of a CNC controller’s executed program (Figure 6). Three of the four vendors that we tested were vulnerable to this attack.
Theft of production information
CNC controllers contain valuable information that help manufacturers cut down costs and remotely track their production processes. This includes what work programs, tools, and production rates are involved in the manufacturing of a specific piece. An attacker, for example, could extract all this data from a CNC controller using dedicated calls that require no authentication or have any resource access controls (Figure 7). We were able to conduct this kind of attack on CNC controllers from all four vendors that we tested.
Shoring up CNC machines’ defenses against cyberthreats
Manufacturing companies stand to gain competitive advantage from harnessing emerging technologies as part of their digital transformation. But in doing so, they could also broaden their attack surface, giving cybercriminals more opportunities to strike. To thwart the threats that come with digitizing production lines, these companies can turn to best practices such as the following for their CNC controllers:
- Installing industrial intrusion prevention and detection systems (IPS/IDSs), which can help manufacturers detect malicious activity in their networks by monitoring traffic in real time.
- Segmenting networks, which can effectively limit access privileges to only users who need them, like end users and operators of CNC machines. Standard security technologies like virtual local area networks (VLANs) and firewalls go a long way toward lessening the exposure of CNC machines’ interfaces from unauthorized access.
- Keeping the software, services, and applications that CNC machines use up to date with the latest patches, which helps deter malicious actors from exploiting vulnerabilities.
- Correctly configuring CNC machines according to the controller vendor’s guidelines and advisories, such as its recommendations regarding enabling encryption and authentication where applicable.
We’ll present this research at the Industrial Control Systems (ICS) Cyber Security Conference in Atlanta this month and at Black Hat Europe in London in December. Learn more about our technical analysis of the security posture of CNC machines in our research paper “The Security Risks Faced by CNC Machines in Industry 4.0.”
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

